Thanks Khaled ismael.
If you have CCNA final exam, please send to me at:
1.
What are two main components of data confidentiality? (Choose two.)
check sum
digital certificates
encapsulation
encryption
hashing
2.
While troubleshooting a problem with an e-mail server, an administrator observes that the switch port used by the server shows "up, line protocol up". The administrator cannot ping the server. At which layer of the OSI model is the problem most likely to be found?
application layer
network layer
data link layer
physical layer
3.
Which combination of authentication and Layer 2 protocol should be used to establish a link between a Cisco and a non-Cisco router without sending authentication information in plain text?
CHAP and HDLC
CHAP and PPP
PAP and HDLC
PAP and PPP
4.
An administrator is configuring a dual stack router with IPv6 and IPv4 using RIPng. The administrator receives an error message when trying to enter the IPv4 routes into RIPng. What is the cause of the problem?
When IPv4 and IPv6 are configured on the same interface, all IPv4 addresses are over-written in favor of the newer technology.
Incorrect IPv4 addresses are entered on the router interfaces.
RIPng is incompatible with dual-stack technology.
IPv4 is incompatible with RIPng.
5.
Which three statements accurately describe attributes of a security policy? (Choose three.)
It creates a basis for legal action if necessary.
It should not be altered once it is implemented.
It defines a process for managing security violations.
It focuses primarily on threats from outside of the organization.
It defines acceptable and unacceptable use of network resources.
It provides step-by-step procedures to harden routers and other network devices.
6.
A technician has been asked to run the Cisco SDM one-step lockdown on a customer router. What will be the result of this process?
It will guarantee that the network is secure.
It will implement all security configurations that Cisco AutoSecure offers.
It will automatically apply all recommended security-related configuration changes.
It will guarantee that all traffic is quarantined and checked for viruses before being forwarded.
7.
Which two functions are provided by the Local Management Interface (LMI) that is used in Frame Relay networks? (Choose two.)
simple flow control
error notification
congestion notification
mapping of DLCIs to network addresses
exchange of information about the status of virtual circuits
8.
Refer to the exhibit. Which statement correctly describes how Router1 processes an FTP request that enters interface s0/0/0 and is destined for an FTP server at IP address 192.168.1.5?
The router matches the incoming packet to the statement that was created by the access-list 201 deny icmp 192.168.1.0 0.0.0.255 any command, continues comparing the packet to the remaining statements in ACL 201 to ensure that no subsequent statements allow FTP, and then the router drops the packet.
The router reaches the end of ACL 101 without matching a condition and drops the packet because there is no statement that was created by the access-list 101 permit ip any any command.
The router matches the incoming packet to the statement that was created by the access-list 101 permit ip any 192.168.1.0 0.0.0.255 command and allows the packet into the router.
It matches the incoming packet to the statement that was created by the access-list 201 permit ip any any command and allows the packet into the router.
9.
Refer to the exhibit. Which statement is true about the CSU/DSU device?
It connects asynchronous devices to a LAN or WAN through network and terminal emulation software.
It uses a multiport internetworking device to switch traffic such as Frame Relay, ATM, or X.25 over the WAN.
It provides termination for the digital signal and ensures connection integrity through error correction and line monitoring.
It converts the digital signals produced by a computer into voice frequencies that can be transmitted over the analog lines of the public telephone network.
10.
Refer to the exhibit. From the output of the show interfaces and ping commands, at which layer of the OSI model is a fault indicated?
application
transport
network
data link
physical
11.
Refer to the exhibit. A network administrator is trying to backup the IOS software on R1 to the TFTP server. He receives the error message that is shown in the exhibit, and cannot ping the TFTP server from R1. What is an action that can help to isolate this problem?
Use correct source file name in the command.
Verify that the TFTP server software is running.
Make sure that there is enough room on the TFTP server for the backup.
Check that R1 has a route to the network where the TFTP server resides.
12.
Refer to the exhibit. Router1 is not able to communicate with its peer that is connected to this interface. Based on the output as shown, what is the most likely cause?
interface reset
unplugged cable
improper LMI type
PPP negotiation failure
13.
A technician is talking to a colleague at a rival company and comparing DSL transfer rates between the two companies. Both companies are in the same city, use the same service provider, and have the same rate/service plan. What is the explanation for why company 1 reports higher download speeds than company 2 reports?
Company 1 only uses microfilters at branch locations.
Company 1 has a lower volume of POTS traffic than company 2 has.
Company 2 is located farther from the service provider than company 1 is.
Company 2 shares the connection to the DSLAM with more clients than company 1 shares with.
14.
Refer to the exhibit. What is placed in the address field in the header of a frame that will travel from the DC router to the Orlando router?
DLCI 123
DLCI 321
10.10.10.25
10.10.10.26
MAC address of the Orlando router
15.
When NAT is in use, what is used to determine the addresses that can be translated on a Cisco router?
access control list
routing protocol
inbound interface
ARP cache
16.
A network administrator is tasked with maintaining two remote locations in the same city. Both locations use the same service provider and have the same service plan for DSL service. When comparing download rates, it is noticed that the location on the East side of town has a faster download rate than the location on the West
side of town. How can this be explained?
The West side has a high volume of POTS traffic.
The West side of town is downloading larger packets.
The service provider is closer to the location on the East side.
More clients share a connection to the DSLAM on the West side.
17.
What are the symptoms when the s0/0/0 interface on a router is attached to an operational CSU/DSU that is generating a clock signal, but the far end router on the point-to-point link has not been activated?
show controllers indicates cable type DCE V.35. show interfaces s0/0/0 indicates serial down, line protocol down.
show controllers indicates cable type DCE V.35. show interfaces s0/0/0 indicates serial up, line protocol down.
show controllers indicates cable type DTE V.35. show interfaces s0/0/0 indicates serial up, line protocol down.
show controllers indicates cable type DTE V.35. show interfaces s0/0/0 indicates serial down, line protocol down.
18.
A technician has been asked to run Cisco SDM one-step lockdown on the router of a customer. What will be the result of this process?
Traffic is only forwarded from SDM-trusted Cisco routers.
Security testing is performed and the results are saved as a text file stored in NVRAM.
The router is tested for potential security problems and any necessary changes are made.
All traffic entering the router is quarantined and checked for viruses before being forwarded.
19.
Refer to the exhibit. Which statement is true about the Frame Relay connection?
The Frame Relay connection is in the process of negotiation.
A congestion control mechanism is enabled on the Frame Relay connection.
The “ACTIVE” status of the Frame Relay connection indicates that the network is experiencing congestion.
Only control FECN and BECN bits are sent over the Frame Relay connection. No data traffic traverses the link.
20.
Which two statements are true about creating and applying access lists? (Choose two.)
There is an implicit deny at the end of all access lists.
One access list per port, per protocol, per direction is permitted.
Access list entries should filter in the order from general to specific.
The term "inbound" refers to traffic that enters the network from the router interface where the ACL is applied.
Standard ACLs should be applied closest to the source while extended ACLs should be applied closest to the destination.
21.
A system administrator must provide Internet connectivity for ten hosts in a small remote office. The ISP has assigned two public IP addresses to this remote office. How can the system administrator configure the router to provide Internet access to all ten users at the same time?
Configure static NAT.
Configure dynamic NAT.
Configure static NAT with overload.
Configure dynamic NAT with overload.
22.
What are two effective measures for securing routers? (Choose two.)
Protect all active router interfaces by configuring them as passive interfaces.
Configure remote administration through VTY lines for Telnet access.
Use quotes or phrases to create pass phrases.
Disable the HTTP server service.
Enable SNMP traps.
23.
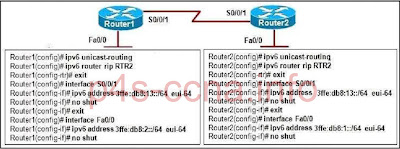
Refer to the exhibit. A network administrator has issued the commands that are shown on Router1 and Router2. A later review of the routing tables reveals that neither router is learning the LAN network of the neighbor router. What is most likely the problem with the RIPng configuration?
The serial interfaces are in different subnets.
The RIPng process is not enabled on interfaces.
The RIPng processes do not match between Router1 and Router2.
The RIPng network command is missing from the IPv6 RIP configuration.
24.
Because of a remote-procedure call failure, a user is unable to access an NFS server. At what layer of the TCP/IP model does this problem occur?
network layer
data link layer
physical layer
application layer
25.
What will be the result of adding the command ip dhcp excluded-address 192.168.24.1 192.168.24.5 to the configuration of a local router that has been configured as a DHCP server?
Traffic that is destined for 192.168.24.1 and 192.168.24.5 will be dropped by the router.
Traffic will not be routed from clients with addresses between 192.168.24.1 and 192.168.24.5.
The DHCP server will not issue the addresses ranging from 192.168.24.1 to 192.168.24.5.
The router will ignore all traffic that comes from the DHCP servers with addresses 192.168.24.1 and 192.168.24.5.
26.
Refer to the exhibit. A network administrator is trying to configure a router to use SDM. After this configuration shown in the exhibit is applied, the SDM interface of the router is still not accessible. What is the cause of the problem?
The username and password are not configured correctly.
The authentication method is not configured correctly.
The HTTP timeout policy is not configured correctly.
The vtys are not configured correctly.
27.
Refer to the exhibit. A technician issues the show interface s0/0/0 command on R1 while troubleshooting a network problem. What two conclusions can be determined by from the output shown? (Choose two.)
The bandwidth has been set to the value of a T1 line.
This interface should be configured for PPP encapsulation.
There is no failure indicated in an OSI Layer 1 or Layer 2.
The physical connection between the two routers has failed.
The IP address of S0/0/0 is invalid, given the subnet mask being used.
28.
Refer to the exhibit. Which DHCP requests will R1 answer?
all DHCP requests that R1 receives
requests that are broadcast to 10.0.1.255
DNS requests with a destination of 10.0.1.3
requests that are received on the FastEthernet 0/0 interface
requests that come from any networks that are not listed as excluded
29.
Refer to the exhibit. Why are the routers unable to establish a PPP session?
The usernames are misconfigured.
The IP addresses are on different subnets.
The clock rate is configured on the wrong end of the link.
The CHAP passwords must be different on the two routers.
Interface serial 0/0/0 on Router1 must connect to interface serial 0/0/1 on Router2.
30.
A network administrator is instructing a technician on best practices for applying ACLs. Which suggestion should the administrator provide?
Named ACLs are less efficient than numbered ACLs.
Standard ACLs should be applied closest to the core layer.
ACLs applied to outbound interfaces are the most efficient.
Extended ACLs should be applied closest to the source that is specified by the ACL.
31.
Which variable is permitted or denied by a standard access control list?
protocol type
source IP address
source MAC address
destination IP address
destination MAC address
32.
What are two LCP options that can be configured for PPP? (Choose two.)
EAP
CHAP
IPCP
CDPCP
stacker
33.
What can a network administrator do to recover from a lost router password?
use the copy tftp: flash: command
boot the router to bootROM mode and enter the b command to load the IOS manually
telnet from another router and issue the show running-config command to view the password
boot the router to ROM monitor mode and configure the router to ignore the startup configuration when it initializes
34.
Refer to the exhibit. An ACL called Managers already exists on this router. What happens if the network administrator issues the commands as shown in the exhibit?
The new ACL overwrites the existing ACL.
The network administrator will receive an error message.
The existing ACL is modified to include the new command.
A second Managers ACL is created that contains only the new command.
35.
Which statement is true about wildcard masks?
Inverting the subnet mask will always create the wildcard mask.
The wildcard mask performs the same function as a subnet mask.
A network or subnet bit is identified by a "1" in the wildcard mask.
IP address bits that must be checked are identified by a "0" in the wildcard mask.
36.
Refer to the exhibit. Branch A has a non-Cisco router that is using IETF encapsulation and Branch B has a Cisco router. After the commands that are shown are entered, R1 and R2 fail to establish the PVC. The R2 LMI is Cisco, and the R1 LMI is ANSI. The LMI is successfully established at both locations. Why is the PVC failing?
The PVC to R1 must be point-to-point.
LMI types must match on each end of a PVC.
The frame relay PVCs cannot be established between Cisco and non-Cisco routers.
The IETF parameter is missing from the frame-relay map ip 10.10.10.1 201 command.
37.
When configuring a Frame Relay connection, what is the purpose of Inverse ARP?
to assign a DLCI to a remote peer
to disable peer requests from determining local Layer 3 addresses
to negotiate LMI encapsulations between local and remote Frame Relay peers
to create a mapping of DLCI to Layer 3 addresses that belong to remote peers
38.
Refer to the exhibit. A network administrator is tasked with completing the Frame Relay topology that interconnects two remote sites. How should the point-to-point subinterfaces be configured on HQ to complete the topology?
frame-relay interface-dlci 103 on Serial 0/0/0.1
frame-relay interface-dlci 203 on Serial 0/0/0.2
frame-relay interface-dlci 301 on Serial 0/0/0.1
frame-relay interface-dlci 302 on Serial 0/0/0.2
frame-relay map ip 192.168.1.1 103 broadcast on Serial 0/0/0.1
frame-relay map ip 192.168.2.2 203 broadcast on Serial 0/0/0.2
frame-relay map ip 192.168.1.1 301 broadcast on Serial 0/0/0.1
frame-relay map ip 192.168.2.2 302 broadcast on Serial 0/0/0.2
39.
A technician is editing and reapplying ACL 115 to a router, what is the result of adding the command access-list 115 permit tcp any 172.16.0.0 0.0.255.255 established to the ACL when it is reapplied to the router?
All traffic that comes from 172.16.0.0/16 will be allowed.
All TCP traffic that is destined for 172.16.0.0/16 is permitted.
Any SYN packets that are sent to 172.16.0.0/16 will be permitted.
Responses to traffic that originates from the 172.16.0.0/16 network are allowed.
40.
Which encapsulation protocol when deployed on a Cisco router over a serial interface is only compatible with another Cisco router?
PPP
SLIP
HDLC
Frame Relay
41.
Refer to the exhibit. Partial results of the show access-lists and show ip interface FastEthernet 0/1 commands for router Router1 are shown. There are no other ACLs in effect. Host A is unable to telnet to host B. Which action will correct the problem but still restrict other traffic between the two networks?
Apply the ACL in the inbound direction.
Apply the ACL on the FastEthernet 0/0 interface.
Reverse the order of the TCP protocol statements in the ACL.
Modify the second entry in the list to permit tcp host 172.16.10.10 any eq telnet .
42.
Refer to the exhibit. Company ABC expanded its business and recently opened a new branch office in another country. IPv6 addresses have been used for the company network. The data servers Server1 and Server2 run applications which require end-to-end functionality, with unmodified packets that are forwarded from the source to the destination. The edge routers R1 and R2 support dual stack configuration. What solution should be deployed at the edge of the company network in order to successfully interconnect both offices?
a new WAN service supporting only IPv6
NAT overload to map inside IPv6 addresses to outside IPv4 address
a manually configured IPv6 tunnel between the edge routers R1 and R2
static NAT to map inside IPv6 addresses of the servers to an outside IPv4 address and dynamic NAT for
the rest of the inside IPv6 addresses
43.
Refer to the exhibit. Communication between two peers has failed. Based on the output that is shown, what is the most likely cause?
interface reset
unplugged cable
improper LMI type
PPP negotiation failure
44.
Refer to the exhibit. A host connected to Fa0/0 is unable to acquire an IP address from this DHCP server. The output of the debug ip dhcp server command shows "DHCPD: there is no address pool for 192.168.1.1". What is the problem?
The 192.168.1.1 address has not been excluded from the DHCP pool.
The pool of addresses for the 192 Network pool is incorrect.
The default router for the 192Network pool is incorrect.
The 192.168.1.1 address is already configured on Fa0/0.
45.
What are two major characteristics of a worm? (Choose two.)
exploits known vulnerabilities
attaches itself to another program
executed by a predefined time or event
masquerades as an accepted program
copies itself to the host and selects new targets
46.
While configuring a Frame Relay connection, when should a static Frame Relay map be used?
the remote router is a non-Cisco router
the local router is configured with subinterfaces
broadcast traffic and multicast traffic over the PVC must be controlled
globally significant rather than locally significant DLCIs are being used
47.
What is the result when the command permit tcp 192.168.4.0 0.0.3.255 any eq 23 is entered in a named access control list and applied on the inbound interface of a router?
All traffic from 192.168.4.0/24 larger than 23 bytes is permitted.
FTP traffic from the 192.168.4.0/24 network is permitted.
TCP traffic destined to 192.168.4.0/24 network is permitted.
Telnet traffic originating from 192.168.4.0/22 is permitted out.
48.
Where does a service provider assume responsibility from a customer for a WAN connection?
local loop
DTE cable on router
demarcation point
demilitarized zone
49.
Refer to the exhibit. The network administrator creates a standard access control list on Router1 to prohibit traffic from the 172.16.1.0/24 network from reaching the 172.16.2.0/24 network while still permitting Internet access for all networks. On which router interface and in which direction should it be applied?
interface Fa0/0, inbound
interface Fa0/0, outbound
interface Fa0/1, inbound
interface Fa0/1, outbound
50.
A network administrator has changed the VLAN configurations on his network switches over the past weekend. How can the administrator determine if the additions and changes improved performance and availability on the company intranet?
Conduct a performance test and compare with the baseline that was established previously.
Interview departmental secretaries and determine if they think load time for web pages has improved.
Determine performance on the intranet by monitoring load times of company web pages from remote sites.
Compare the hit counts on the company web server for the current week to the values that were recorded in previous weeks.
51.
Refer to the exhibit. What can be concluded from the exhibited output of the debug ip nat command?
The 10.10.10.75 host is exchanging packets with the 192.168.0.10 host.
The native 10.1.200.254 address is being translated to 192.168.0.10.
The 192.168.0.0/24 network is the inside network.
Port address translation is in effect.
52.
Refer to the exhibit. RIPv2 has been configured on all routers in the network. Routers R1 and R3 do not receive RIP routing updates. On the basis of the provided configuration, what should be enabled on router R2 to remedy the problem?
proxy ARP
CDP updates
SNMP services
RIP authentication




 2:35 AM
2:35 AM
 Unknown
Unknown